There are many situations where you may encounter access to some . For example, some employers block access to social media and entertainment sites to prevent workers from being distracted from their duties. A similar situation occurs in educational institutions. In this article we will talk about how to access a blocked site by bypassing the blocking.
Option #1: Go to a blocked site using Google Translator.
Google provides a free online translator, which is available at translate.google.com. The main feature of this translator is that it can be used to translate not only text, but also entire web pages.
In order to translate a web page, simply enter its address in the translation field and click on the translate button. After this, the specified web page with the already translated text will load.
As a rule, access to Google resources is not blocked, so this feature of Google Translator can be used to gain access to blocked sites. Enter the address of the blocked site in the translator window and click on the “Translate” button or click on the link that appears on the right side of the page.
Once the site loads, you can use it as usual. All links will work and you will be able to navigate to other pages on the site.
Option number 2. Open a blocked site using anonymizers.
Anonymizers are sites that allow you to secretly browse other websites, playing the role of an intermediary between you and the final site. In general, this method is very similar to the previous one. You go to the anonymizer’s website, enter the address of the site you need and click on the “Go” button. After this, the page you need is loaded.

The most popular anonymizers:
Option #3: View a blocked site using the search engine cache.
All search engines save a cache version of indexed pages. This feature can be used to gain access to blocked sites.

Enter a search query that will lead you to the desired page, after which you need to open the saved cache in the search engine results. In Goole this function is called “Saved Copy”; in the Yandex search engine it is simply “Copy”.
From other people, but we often find ourselves in their place. And if many are still willing to put up with the inaccessibility of certain websites at work, then at home - excuse me. However, neither paying for your home internet on time nor civil rights and freedom of speech guarantee us unfettered access to all web content. Resources included in the register of prohibited in Russia, for example, many popular torrent trackers, are closed from us with seven locks.
Fortunately, blocking sites, even at the provider level, is not a bastion. No matter how hard Roskomnadzor tries, we will still find the keys to them. Today you will learn how to access a blocked site in all available ways without breaking the law.
An anonymizer is an intermediary node (web proxy) between the user and the target resource, designed for anonymous surfing of the network, as well as access to blocked sites.
How anonymizers help bypass blocking: when opening any Internet page, the request is transmitted to the provider’s devices, where the name and IP of the site are checked against blacklists. If access to the resource is open, the request is sent to the target server and the browser downloads the content. If closed, the provider redirects the user to a stub page. For MTS it looks like this:
Beeline has this:

Other providers have their own way, but the essence of the message is the same: access to the site is prohibited. And period.
When accessing the same node through an anonymizer, the provider’s network devices see only the anonymizer’s data. And since it is not on the black list, nothing limits the loading of the target resource.
Using the anonymizer is very simple:
- open its page;
- In the “Open” field, enter the URL of the target site and click the go button.

Unfortunately, today many popular anonymizers are also blocked. Only the most harmless ones remain - intended for opening VKontakte, Odnoklassniki, Facebook and other similar portals that are usually not allowed to be visited at work. And of those that help unblock Roskomnadzor blacklist sites, the absolute majority are closed.
At the end of January and beginning of February 2017, the following free anonymizers are available:
- NoBlockMe - provides alternative access to social networks and LiveJournal.
- Pingway - for access to social networks and YoutTube.
- Anonim.pro - unblocks social networks, YouTube, dating sites, Avito, Tanki online.
- Anonymous
- Anonymizer.ru - for any Internet resources.
- Guardster is also for everything.
When opening a website through an anonymizer, you may encounter problems:
- Incomplete loading of content. The page may open without pictures, audio or video, buttons may not be pressed, menus may not work, etc.
- Displaying pages in a distorted form - with blocks shifted, text creeping into pictures, etc., up to complete unreadability.
- Inaccessibility of web resources that transmit data via the https protocol.
- Excessively intrusive display of advertising - huge banners, pop-up windows, constant transfers to other web resources. It is possible to covertly install adware (from the word adware - advertising software) and spyware on your computer, which you will then have to fight for a long time.
To reduce the likelihood of this, use anonymizers tailored for the content you need, for example, social networks. Or use other methods to bypass the blocking.
Browser tricks
Regular web browsers do not have special tools that allow you to open blocked sites, but there are options for which this action is a “side” action. In Opera and Yandex Browser, such a tool is the Turbo traffic saving mode. So, if you want to speed up the opening of slow-loading pages, you will receive a pleasant bonus in the form of free access, for example, to Rutrecker.org.
In Opera, the Turbo option is enabled in the main menu.

In Yandex Browser - in the main settings.

Google Chrome and Mozilla Firefox do not have a Turbo mode, but Google Translate may be useful for our purposes. The translated site opens in a separate frame, and access to it is no longer blocked.
If you have never used Google Translator, let us explain how to do it: insert the URL of the page you want to open into the left window and select the original language. Even if the page is in Russian, the original should be a foreign language, for example, English, and the translation language should be Russian. Then click the “Translate” button.

The result of opening Rutrecker.org, as can be seen in the screenshot, is quite decent.

Another way to bypass site blocking is to enter not a name, but an IP address in the address bar of the browser, which Whois services will help determine. For example, this one.
Unfortunately, browser “tricks” are not 100% effective: Google does not translate some sites, and in Turbo mode they also remain blocked, not only by name, but also by IP.
Special browser extensions
If you are unable to access the site using your browser's own means, a third-party extension will help solve the problem. One of the most popular tools for this purpose is FriGate (the link is given to the Chrome store, but it exists for other browsers).

FriGate encrypts and routes some of your web browser traffic through its own VPN server. This not only restores access to sites when blocked, but also speeds up the connection.
In addition to FriGate, there are many free extensions that have similar functions. Here are some of them:
Some of them require configuration after installation, for example, creating custom lists of web resources and rules, while others have only an on/off button and nothing more. Some extensions provide a choice of 3-4 available proxy servers, others do not. Use what suits you best, since there are many options. At least one will work.
Free VPN clients for Windows and other platforms
The main purpose of a VPN is to create closed communication channels to protect network traffic from leakage and outside access. However, this technology is also used to visit blocked Internet pages. Unlike anonymizers, which redirect the request to one site in the right direction, and browser extensions, which pass the traffic of one web browser through a proxy, VPN applications direct all network traffic of the computer into a closed channel.
Services for accessing VPN servers through a client program are usually paid (cost $1-50 per month depending on the channel bandwidth and the availability of additional options), but there are several free ones.
The best free VPN client for Windows, Mac OS X, Linux and mobile platforms, according to the author, is CyberGhost 6. Here are its most significant advantages in comparison with analogues:
- There are no traffic volume restrictions. Most free applications of this format limit traffic to approximately 500 mb per month or for the entire period of use. If you need more, sign up for a paid subscription.
- Quite high connection speed. Most free VPNs reduce it to a minimum.
- Large selection of available servers around the globe. Many free analogues offer only one server, which is located somewhere in the USA and is constantly overloaded.
- Several pre-installed profiles for different tasks (only half are available without payment, but this is quite enough for most tasks).
- Can be used to access any type of web resource. Supports almost all types of traffic: video streaming, online games, social networks, etc., limits p2p.
- Easy to learn for beginners.
- Russified.
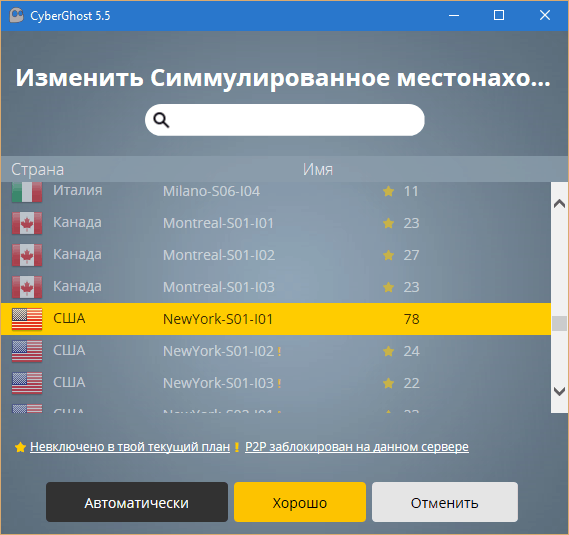
To get to a closed site using CyberGhost 6, just launch the program and select one of the available profiles.

When you select the anonymous surfing option (yellow tile), you just need to set the browser boot mode (normal or incognito) and specify the desired VPN server.

When choosing to unblock basic websites (blue tile), you just need to click on the corresponding icon.

Tor browser), which implements onion routing technology for Internet traffic.
The principle of data transmission over the Tor network differs from the usual one in that all transmitted information is encrypted multiple times (layer-by-layer) and follows a randomly built chain of proxy servers absolutely anonymously. Neither the intermediate node nor the end node receives information about the sender of the request and the route of the traffic. Each server reads exactly the information that is necessary to transmit the packet to the next node (figuratively removes its own layer of onion peel). Such a system provides the user with maximum privacy and makes tracking his traffic, if not impossible, then very difficult.
Not a single method of blocking web resources can withstand the onslaught of Tor. But only if Tor itself is not closed. Unfortunately, in Kazakhstan and Belarus, many connections of this wonderful instrument are blocked at the state level. In fact, this makes it impossible for the majority of the inhabitants of these countries to use it.
Tor is not yet banned in Russia, and its use does not threaten you with any sanctions.
Do you like that someone decides for you what sites to visit, what to read, what to watch, what to download, who to communicate with and how to live? Definitely not for me. Meanwhile, the practice of blocking web resources for certain offenses is spreading wider and wider.
Almost every week we hear about the closure of one or another Internet portal from Russian visitors. Plus, employers make their contribution. We won’t sit idly by looking at this! Let's talk about how to bypass website blocking in simple and free ways.
How to bypass website blocking: fast, easy and free
VPN
VPN(virtual private networks) are used not only for access to a corporate or private Intranet, but also for anonymity on the World Wide Web. Unlike browser extensions, they pass all computer or local network traffic through a proxy.
To surf closed sites, you need to install a VPN application. Most of them, unfortunately, are paid, but I have selected a few free ones for you.
The best free VPN service, in my opinion, is Freemer.org. He:
- Russian-speaking.
- Understandable.
- Has no restrictions on traffic volume.
- Maintains a directory of frequently visited sites, which you can create yourself. You simply go to Freemer.org, add the desired web resource to the list, and after a while it appears in the application. This is more convenient than using browser bookmarks.
- Works automatically. It has no manual settings, which means it won’t allow you to get confused or do something wrong.
- Always chooses a server that can provide the most stable and fastest connection to the desired web resource.
- Reliably protects your real IP and all transmitted data from leakage into the hands of strangers.
How to use Freemer
To add a blocked site to the Freemer directory, go to , enter its URL in the field shown in the screenshot and click the add button.
To go to any resource already included in the list, launch the application and click “ Site directory“. Or enter its URL in the address bar and click “ Find“.

Having found the desired website in the directory, simply click on its thumbnail. In a few seconds it will open on the same page.

Do you want to get to RuTracker.org? No problem! And by clicking on the star in the upper right corner of the window, you will add it to your visual bookmarks in the Freemer browser.

To get additional information about any site from the catalog - description, search tags, screenshot of the main page, click on the “ button on the thumbnail” More details“.

To quickly go to this site from the description page, click “ Play“. It's that simple!
I would put it in second place in the list of the best VPN services for the fact that it:
- cross-platform – works under Windows, Linux, OS X, Android and iOS;
- carries out proxying through servers of different countries;
- does not place restrictions on the volume of traffic;
- provides good connection speed;
- reliably hides the user’s original data;
- makes it possible to replace information about the operating system and web browser.
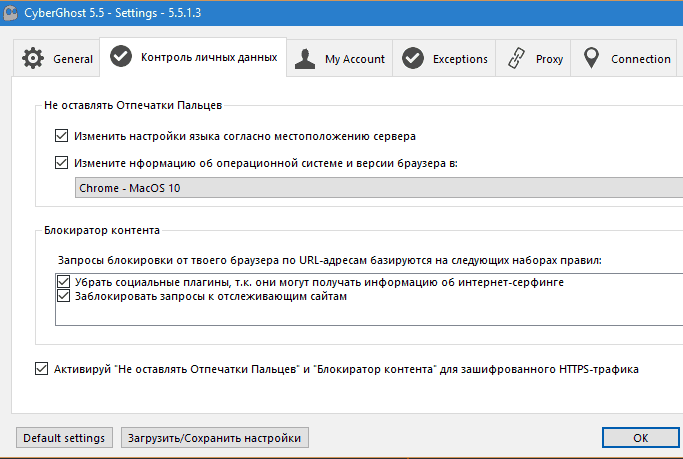
Other VPN service apps:
Bypassing blocking with the help of anonymizers is convenient and beautiful, but not without a flaw. The disadvantage of all such services is limited support: for example, they are useless for accessing gaming and multimedia portals. Often they do not open multi-structured web resources well - with numerous scripts and complex transitions. It happens that the design of pages is distorted - blocks are shifted and text spreads out. In short, it is better to use anonymizers for what they are designed for.
Browser turbo mode
Turbo mode, which speeds up the loading of web content, is also used to access blocked sites. True, not to everyone and not everywhere. Working in turbo mode, the browser routes traffic not along the usual path, but through a proxy server (intermediate network node), where data compression occurs. Bypassing blocking is an undocumented feature and a nice gift for users.
Option " Turbo"is available by default in Opera, Yandex.Browser and some web browsers for mobile platforms. In others it must be installed as an extension.
In Opera, the turbo mode activation button is located in the main menu:

In Yandex.Browser, the function is enabled in the settings:

The turbo extension for Google Chrome is called “” (Traffic Saving), and Mozilla Firefox, unfortunately, has no analogues today.
Browser extensions
To access blocked resources, it is convenient to use anonymizers in the form of browser extensions that direct web traffic first to proxy servers, and from there to the vastness of the global network under changed IPs. So, if the site is closed to visitors from Russia, the IP address of another state will serve as the “key to the front door.”
The friGate CDN extension is designed to remove the blocking of resources that are subject to sanctions by government agencies, by the way, today our favorite ones are among them. The list of disgraced pages is stored in the application itself, and the user has the opportunity to add to it.
Proxy servers are located in different countries. When you open a prohibited page, a small window will show which country you are under the flag of. If you want to select a different server, click on the flag image.

friGate supports Opera, Mozilla Firefox and Google Chrome browsers.
There are other extensions with similar functions:
Unlike friGate, Zenmate, Browsec and Hola encrypt and redirect all browser traffic to servers scattered around the world.
Tor
The last tool in today's review to bypass the blocking is. It uses “onion routing” technology, the essence of which is that all sent information is encrypted multiple times (layer-by-layer) and passes through a chain of intermediate nodes. This provides the highest level of anonymity and guarantees access to any blocked sites, although it significantly slows down communication.
Tor, as a rule, is not needed for constant network surfing, but when all opportunities to get to the treasured resource have been exhausted, only it can save you.
And one more question worries many: by using means of bypassing the blocking, are we breaking the law? No! None of what I talked about in the article is prohibited in Russia. At least today we do not face any punishment for this.
Initially, it was assumed that the Internet was a global network that connected the whole world. However, in reality, many web resources may be blocked in certain regions due to legislative initiatives. What should you do if you still need to access a blocked site? We have collected several reliable and effective methods to bypass blocking of prohibited resources.
1. Opera web browser

Another reliable way to bypass blocking is to use the Tor Browser web browser based on Mozilla Firefox. The Tor browser is a client application for the anonymous network of the same name. To ensure user confidentiality, multi-level encryption and routing of your network traffic over a distributed network are used.
This technology prevents an outside observer of your Internet connection from knowing what websites you visit, prevents sites from knowing your physical location, and also allows you to access blocked web resources.
The main disadvantage of using Tor is the slow connection speed. However, you pay for the anonymity and confidentiality of your personal data. The browser can be used absolutely free and without restrictions.

Some blocking can be done by changing DNS settings. In this case, to bypass the blocking, it is enough to change the DNS server on your computer or router. If you try to visit a blocked site, the third-party DNS server will redirect your traffic through the tunnel. The remote server will assume that you are accessing from the appropriate country, and the site will work.
When you configure DNS on your router, sites will be unblocked on all devices on your home network. In this case, you do not need to constantly change your DNS settings. The connection will be stable for all your traffic.
Google Public DNS is a free, global Domain Name System (DNS) service used as an alternative to your ISP's DNS. Advantages: increased speed, reliability and security of the Internet connection.
Cloudflare DNS - "1.1.1.1" service is focused on speed and privacy protection, providing fast and secure web surfing on the Internet.

Using the following services and instructions, you can create and run your own VPN or proxy server.
Outline VPN is a service that allows any user to create and run their own VPN server and provide other users with access to this server.
3proxy on FreeBSD - a ready-made setup script and step-by-step instructions for renting and quickly setting up a virtual server for a proxy.
Found a typo? Highlight and press Ctrl + Enter
Allowing competent authorities to block access to any Internet resources on the territory of Russia out of court. Officials were given the opportunity to arbitrarily close for users within the country absolutely any site that, for reasons known only to them, seemed “unreliable” and “extremist.” This was clearly demonstrated with all determination and cynicism.
In the early nineties, we naively believed that the times of censorship and persecution for thought crimes were far in the Soviet past, but today in Russia lists of banned books and “extremist materials” are actively being compiled and people are being persecuted who dared to publicly declare their disagreement with the “only true” official point of view. De facto, the fundamental articles 29 and 31 of the Constitution of the Russian Federation, declaring freedom of speech, freedom of thought, freedom of information and demonstration, and article 19 of the Universal Declaration of Human Rights, declaring freedom of information one of the most important political and personal human rights, have been abolished.
Under these conditions, we are forced to return to the topic of bypassing blocking of Internet resources - in order to restore the inalienable constitutional right of citizens of the Russian Federation to freely receive and disseminate information.
1. “Turbo mode” in Opera and “Yandex.Browser”
The simplest and still quite effective way to access sites blocked by your provider is to use the “Turbo” mode built into the Opera and Yandex.Browser browsers. Initially, this mode was intended to speed up page loading on slow connections: traffic from the requested Internet resource is first transmitted to the browser’s Internet servers, where it is compressed and optimized, and only then transmitted to the client’s computer.
In addition to real loading acceleration, this mode allows you to access blocked resources, since for the provider such traffic looks like data from harmless servers, so “Turbo” simultaneously acts as a free proxy anonymizer that does not require any settings at all.
To enable the “Turbo” mode in Opera, you just need to click on the corresponding icon in the lower left corner of the window, and in “Yandex.Browser” you need to go to the settings, click on the “Show additional settings” button at the bottom of the page and find the “Turbo” item.
The problem is that sooner or later the Opera and Yandex Browser servers themselves may be blocked at the provider level, and this function will simply become unavailable. Moreover, in the case of Yandex, whose servers are located on the territory of the Russian Federation, pages that are blocked for display in our country by the content provider itself may not open, which we can already see now: Alexei Navalny’s LiveJournal opens perfectly in Opera (via foreign servers), while Yandex.Browser displays a “stub” about its blocking in Russia.
2. Stealthy and friGate plugins for Chrome and Firefox browsers
If you use Chrome or Firefox browsers, then to access blocked resources you can install the Stealthy plugin, which ensures traffic passes through foreign anonymous proxy servers. To enable the plugin, just click on the corresponding button: green means that Stealthy mode is enabled, red means it is disabled.
Stealthy also has a free online service, but it is less convenient and for some reason does not work as reliably as the plugin.
The main disadvantage of any web proxies is a significant reduction in access and page loading speeds.
4. Virtual Private Network (VPN)
A radical way to gain access to any Internet resources without restrictions is to set up a virtual private network (VPN). As a rule, VPNs encrypt all traffic transmitted through them and redirect it through a whole chain of servers, which provides a very high level of anonymity (unfortunately, not absolute, since many VPN providers undertake to cooperate with law enforcement agencies, which is specifically noted in the user agreement).
In most cases, VPN is a paid service, but there are also simplified services that provide the user with minimal functionality for free. In particular, VPNBook offers completely free services of its virtual private network with support for cross-platform OpenVPN technologies or the PPTP (Point-to-Point Tunneling Protocol) point-to-point tunneling protocol. Both of them are not secure enough if intelligence agencies or professional hackers are interested in you, but they are quite suitable for the average user.
The VPNBook service does not require registration or account creation. Moreover, if you intend to use the PPTP protocol, then you do not even need to install any additional software. It is enough to select a new connection in the network connection settings of the operating system (Windows, Linux, Mac OS, Android, IOS, PS3 are supported) and enter the parameters specified on the VPNBook website. Some providers block the PPTP VPN protocol, in which case you will have to download and install a free OpenVPN client that allows you to bypass this restriction and operates over standard TCP or UDP protocols.
5. Tor Browser
“A classic of the genre” – the Tor browser, which works based on “onion routing” technology. Its meaning is that all transmitted data is repeatedly encrypted and decrypted, passing through a sequence of “onion routers”, each of which redirects it to random routers on the Internet. As a result, the need for guaranteed reliability of each of these routers is lost, since it is impossible to determine where the data was originally transmitted from. Of course, like any other, this technology also has vulnerabilities, but if used correctly, it guarantees a very high level of security.
6. I2P network
An alternative to the Tor network is the second most famous anonymous decentralized distributed network I2P. It is a kind of add-on, a “network within a network,” a set of encrypted tunnels that provide a high level of anonymity and security for all users. I2P provides the ability to access resources both within the network itself and on the “external” Internet, for which, like Tor, special gateways are used.
To access sites via HTTP, you will need to download and install the I2P service and then configure your browser to use an HTTP proxy on IP 127.0.0.1 via port 4444. Detailed instructions, links and descriptions of the I2P network capabilities can be found in the files included with the distribution services. Good brief instructions for installation and configuration can be found


